
Apple has come up with a privacy preserving web traffic relay for its Safari users. When we browse the web, we request DNS queries and our IP address gets sent to the DNS provider as well as the websites we visit. Apple has come up with a solution, which it states is "designed to protect your privacy by ensuring that when you browse the web in Safari". This article aims to explain how this works. iCloud Private Relay has three jobs to play:
Apple claims "no single party—not even Apple—can see both who you are and what sites you're visiting." This means not even the Internet Service Provider (ISP) can snoop on the user. In this article, we'll discuss how this works.
Apple has partnered with Cloudflare and Fastly to set up oblivious DNS, which we'll understand from the below diagram 👇
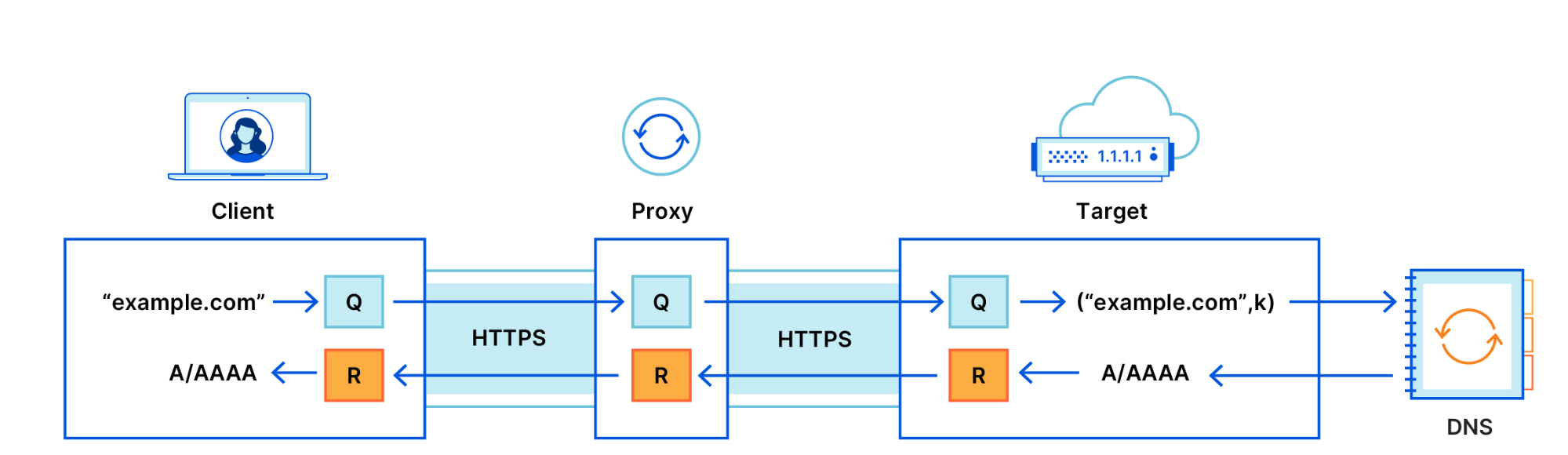
The user establishes an HTTPS connection with a proxy, which forwards the message from the user to the target. The user acts as the same in the case of DNS and DoH, and holds the encryption key (to encrypt queries to the target) as well as the decryption key (to decrypt the DNS's response). Cloudflare tells encryption and proxying has the following guarantees:
These three guarantees improve user privacy while maintaining the security and integrity of DNS queries. However, each of these guarantees relies on one fundamental property — that the proxy and the target servers do not collude. So long as there is no collusion, an attacker succeeds only if both the proxy and target are compromised.
Cloudflare tells it also adds end-to-end encryption between the user and the target, over TLS/HTTPS, to not make it anyhow possible for the ISP to know what sites is the user visiting or what is his/her IP address. The "target" here refers to the website as well as the DNS provider.
Long story short, this means Cloudflare (1.1.1.1) as well as the website will not receive the user's IP address, having a great positive impact on user's privacy.
Note: The proxy here is the Egress proxy, which we'll discuss in the third section.
This upgrade is obvious, with HTTP the ISP can know exactly what the user is doing. Making this upgrade shifts a non-encrypted traffic to an encrypted traffic, helping in maintaining the "web of trust".
In order to hide the user's IP address, Apple sets up two proxies:
The Ingress proxy does the following things:
The Egress proxy does the following things:
After understanding these two proxies, let's dive into understanding how these works in order to protect user privacy with the below diagram 👇
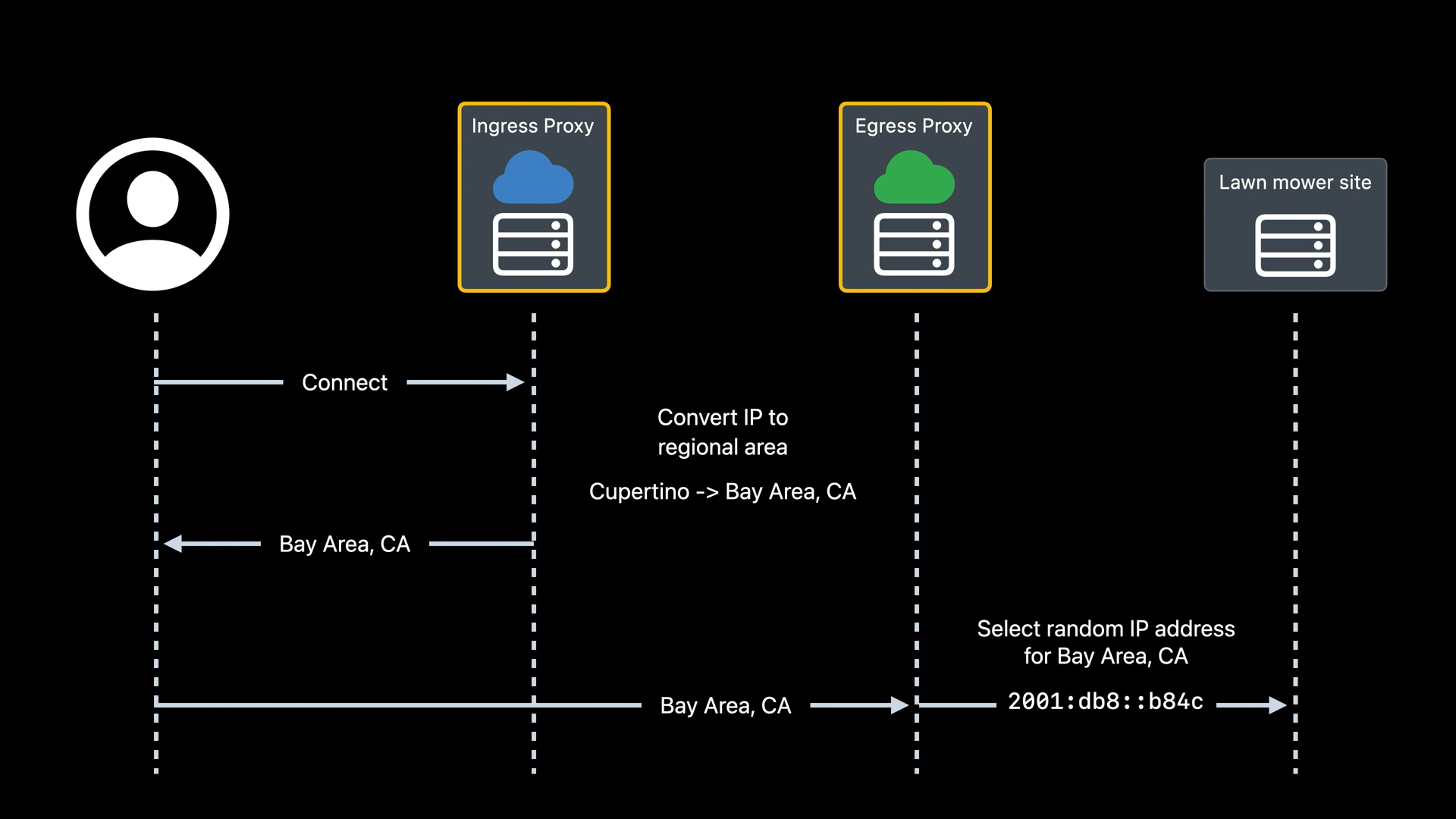
The user connects to the Ingress proxy, which gets the IP address to know the area in which the user lives, via HTTPS. Then, the user requests to the Egress proxy via HTTPS, which knows the area where the user lives, and not the IP address with the requested website, and prevents the Ingress proxy from getting information about the requested website. With knowing the area in which the user lives, the Egress proxy assigns a random IP address from the area to the traffic, not using user's real IP address, and requests to the website, taking the information, moving back forth.
In order to make sure only one party doesn't have control over both the proxies, it may happen later in the future that the ingress proxy is operated by Apple and the egress proxy from Cloudflare or Fastly.
The whole iCloud Private Relay looks a good privacy step from Apple protecting user privacy to a great extent. From this the user can get assured:
Currently iCloud Private Relay is in its Beta stage (in iOS 15, iPadOS 15, and macOS Monterey) and not available in all countries and regions. It requires an iCloud+ subscription.